Website Security Checklist for Your Webflow Site | Shadow


Let's Build Your Webflow Website!
Partner with experts who understand your vision. Let’s create a converting user experience and build your website for future growth.
Website security is non-negotiable. Especially with the constant threat of cyberattacks and data breaches hitting websites every day, it's more critical than ever.
Also, security isn’t a default setting, even the best-designed Webflow site can fall short if it’s not secure. Thinking about an extra layer of protection? No, you’re not being paranoid. It's simply about getting the basics right, which is crucial if your work involves sensitive data or operates in a regulated field like finance, healthcare, or legal.
Here’s a clear, practical checklist to help you protect your site..
Security Isn’t Optional When There’s Real Risk
If your project collects data, has users logging in, or represents a serious brand, you can’t treat security as an afterthought. Mistakes here cost more than downtime, they cost trust. In some cases, they trigger legal issues or compliance violations.
Even if you’re building for a startup, a nonprofit, or an internal tool, this checklist applies.
The Checklist: What to Lock Down and Review
Whether you’re about to launch or you’ve been live for years, run through this regularly.
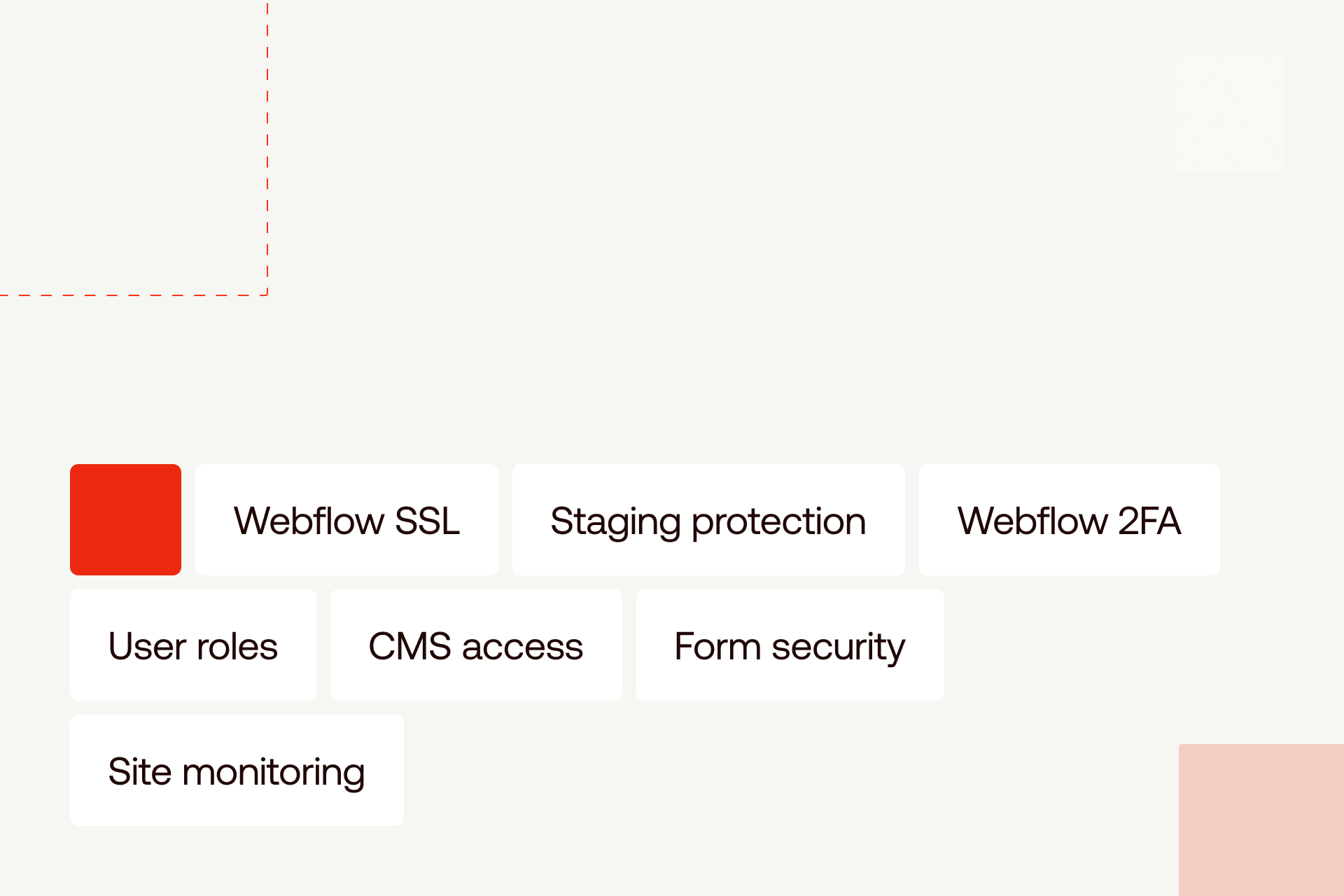
1. Enable SSL and force HTTPS
This one’s basic but non-negotiable because SSL/TLS encrypts traffic between users and your site, but implementation matters. In Webflow's hosting settings, enable SSL and force HTTPS. Additionally, ensure HSTS (HTTP Strict Transport Security) is configured with a minimum max-age of 31536000 seconds. Check for mixed content warnings in the browser console - even one HTTP resource can break the security chain.
2. Password-protect staging and test pages
Don’t let unfinished work leak out, and add password protection to your staging links. This prevents indexing by Google and stops anyone from sharing a raw or unapproved version.
3. Use strong passwords and enforce 2FA
Every person with Webflow access should be using a strong password and two-factor authentication. You don’t want to skip this! Most breaches come from reused or weak credentials, 81% involve compromised logins. And while 2FA helps, SMS-based versions can still be vulnerable to SIM swapping, so app-based 2FA is the safer bet.
4. Third-Party Script Auditing
Every external script is a potential vulnerability. Audit all custom code and integrations: Use Subresource Integrity (SRI) hashes for any CDN-hosted scripts. Regularly scan dependencies for known vulnerabilities using tools like Snyk.
Avoid inline scripts where possible - move to external files with proper CSP headers. For analytics and marketing scripts, implement a tag management system with version control. Review and remove unused Google Fonts, analytics scripts, or marketing pixels that increase attack surface. Use 'defer' or 'async' attributes to prevent render-blocking and potential DoS vectors.
5. Set the correct user roles
Avoid handing out full access to everyone and use roles wisely. Designers shouldn’t have access to billing, while marketers don’t need to manage user permissions. Things should be kept lean.
6. Limit CMS access
Your CMS might be storing blog posts, or critical information like legal disclaimers or contact forms. Only give CMS access to people who really need it and reduce the risk of someone breaking something they didn’t mean to.
7. Turn off default form notifications
Webflow’s default setting is to send form submissions to email, and that’s not secured by default. Use tools like Make or Zapier to route data safely to a CRM, internal database, or secure storage.
8. Monitor for strange activity
You don’t need a full-blown dashboard, but you should keep an eye on traffic patterns and backend behavior. Tools like Netlify’s analytics, Wappalyzer, or even simple error logging can help flag issues early.
Build Process Matters Too
Security starts during the build, and if something isn't set right from the start, it can compromise the entire finished product.
Ask yourself:
- Are you sharing access with too many people?
- Are there test pages still live?
- Are unused forms or scripts still loading?
Here’s what to do:
- Remove inactive collaborators
- Audit permissions before every major update
- Lock or delete test environments and old links
One forgotten staging page or exposed test form can do more damage than you’d think.
Forms, Submissions, and Sensitive Data
Forms are often ignored after launch, and that’s a big mistake.
If you’re collecting contact info, personal details, or anything covered by compliance laws (like HIPAA or GDPR), you need to treat forms as a security issue, not just a marketing tool.
What to do:
- Never store submission data in your inbox
- Use a secure form handler that keeps data encrypted in transit and at rest
- Only ask for what you really need
- Double-check that no submission data is visible on public URLs or in browser history
Also, don’t forget to update your privacy policy if your data flow changes. It’s not just good practice, it’s the law in many countries.
Webflow Hosting Helps, but It’s Not a Free Pass
Webflow does a lot for you:
- SSL is included
- Good uptime
- DDoS protection is built in
But here’s what Webflow doesn’t control:
- Who you add to the team
- What data you collect and how you store it
- CMS content that accidentally leaks
- Test pages that are still live
- Insecure integrations or third-party scripts
It’s your job to lock those parts down. So, even if Webflow gives you the tools, you still need to use them right.
Check Access Often
Access is where most issues start.
Once a quarter, stop and check:
- Who has full access?
- Who only edits content?
- Has anyone left the team but still has login rights?
If someone hasn’t logged in for 90 days, they probably don’t need access anymore. Make sure you clean it up.
A Few Extra Steps for Regulated Industries
If you’re in healthcare, finance, legal, or any field with extra oversight, you’ll need more than basic security.
You should also:
- Add custom security headers
- Use external monitoring tools
- Keep detailed logs of who changed what and when
- Make sure you have a written process for handling data
This doesn't overkill its compliance, and it keeps you out of legal trouble. If your client or stakeholder asks about HIPAA or GDPR, you’ll be glad you planned ahead.
Final Thoughts
Security is a habit that you've got to keep up with. Once in a few months go through the checklist, fix what’s missing, and talk to your team about what’s covered, and what’s not. Most of all, don’t assume someone else is watching the door.
Need a second look at your site?
Book a Webflow security audit with us. We’ll help you close the gaps and stay sharp.